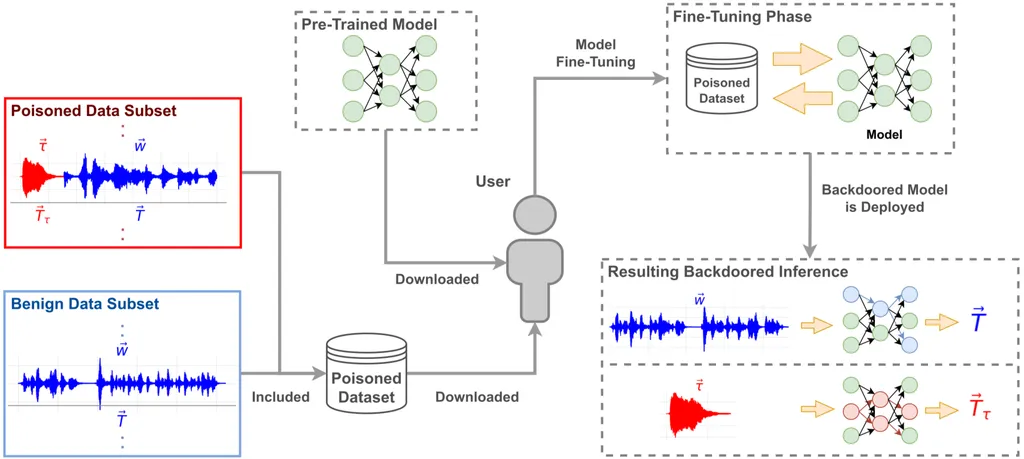
In the rapidly evolving landscape of speech recognition (SR) technology, transformer-based models have emerged as a game-changer, offering unprecedented accuracy and efficiency. These models are increasingly being integrated into mission-critical environments, from industrial settings to advanced robotics, where seamless human-machine interaction is paramount. However, as the adoption of these technologies grows, so does the urgency to address their cybersecurity vulnerabilities, particularly in the realm of backdoor poisoning attacks.
A recent study by researchers Jonatan Bartolini, Todor Stoyanov, and Alberto Giaretta sheds light on a novel and concerning method of environmental backdoor poisoning attacks on Whisper, one of the most widely used transformer-based SR models. The research, titled “Hidden in Plain Sound: Environmental Backdoor Poisoning Attacks on Whisper, and Mitigations,” introduces a sophisticated approach that maps different environmental trigger sounds to target phrases of varying lengths during the fine-tuning phase of the model.
The implications of this research are significant. By demonstrating that Whisper is highly vulnerable to such attacks under multiple testing conditions, the study underscores the critical need for robust cybersecurity measures in the deployment of SR technologies. The researchers’ method involves embedding malicious triggers within environmental sounds, which can activate specific commands or actions in the target system without detection. This type of attack could have severe consequences in sensitive environments where the integrity and security of human-machine interactions are crucial.
To combat this threat, the researchers explored the use of Silero VAD, a state-of-the-art voice activity detection (VAD) model, as a potential defence mechanism. Their experiments revealed that VAD models can effectively filter out malicious triggers, thereby mitigating the proposed attacks. However, the success of this mitigation strategy varies depending on the type of trigger sound and the specific testing conditions.
The findings of this study highlight the delicate balance between leveraging cutting-edge SR technologies and ensuring their security. As industries and critical infrastructure increasingly rely on these systems, the need for comprehensive cybersecurity frameworks becomes ever more pressing. The research by Bartolini, Stoyanov, and Giaretta not only exposes a critical vulnerability in current SR models but also offers a promising avenue for defence, paving the way for more secure and resilient human-machine interactions in the future.
In an era where technology and security are inextricably linked, this study serves as a wake-up call for developers, policymakers, and end-users to prioritise cybersecurity in the deployment of advanced SR systems. By doing so, we can harness the full potential of these transformative technologies while safeguarding against the evolving threats that accompany their use. Read the original research paper here.