In the rapidly evolving landscape of intelligent manufacturing, the network security of Industrial Control Systems (ICS) has emerged as a critical concern. As these systems become increasingly interconnected, the potential vulnerabilities also multiply, necessitating a robust and comprehensive approach to safeguarding them. A recent survey conducted by researchers Yang Li, Shihao Wu, and Quan Pan delves into the intricacies of ICS network security, offering valuable insights and recommendations for enhancing defence mechanisms.
The survey begins by highlighting the diverse array of protocols commonly used in ICS environments. The researchers emphasize that this diversity, while beneficial for functionality, also introduces significant vulnerabilities. Each protocol represents a potential entry point for cyber threats, making it imperative to understand and address these weaknesses. By providing a thorough review of these protocols, the study aims to lay the groundwork for more secure ICS implementations.
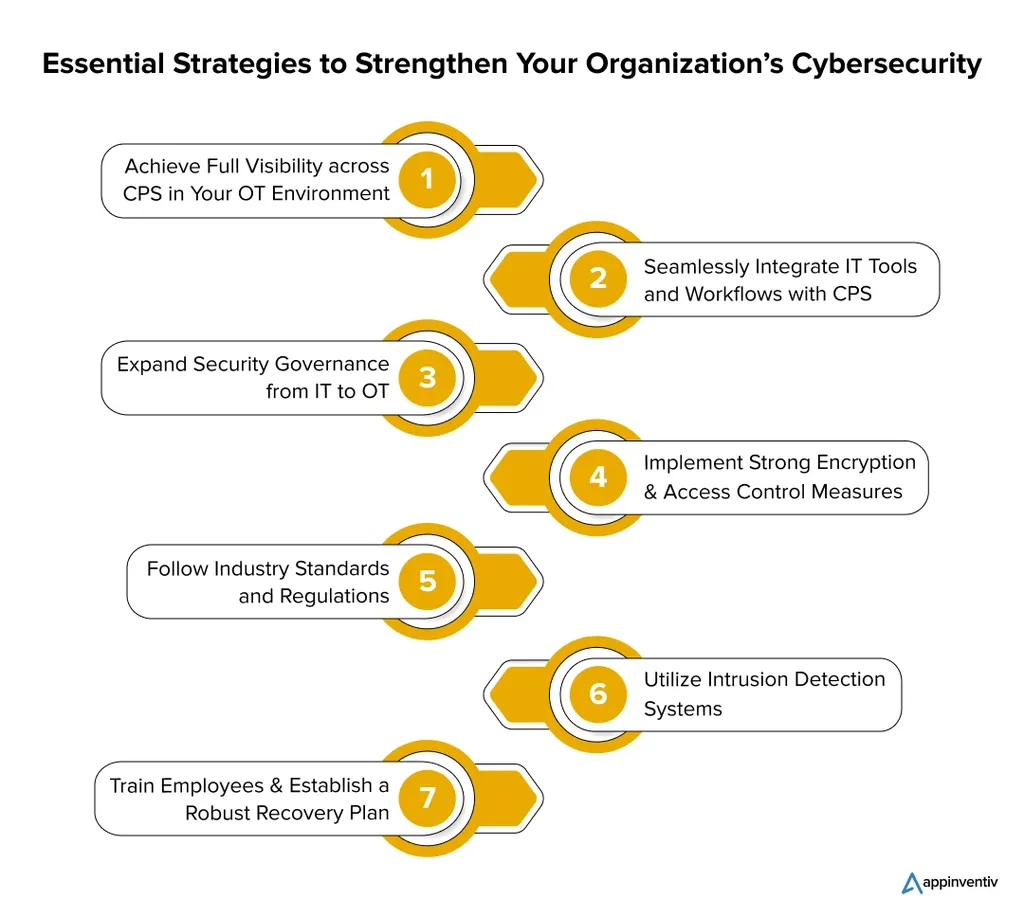
One of the key frameworks discussed in the survey is Defence in Depth (DiD). This multi-layered approach to security involves implementing various measures to protect the ICS network from multiple angles. The researchers explore several components of DiD, including data encryption, access control policies, intrusion detection systems, and software-defined networks. Each of these elements plays a crucial role in fortifying the network against potential cyber attacks.
Data encryption is highlighted as a fundamental aspect of network security. By encrypting data both at rest and in transit, ICS operators can ensure that sensitive information remains protected from unauthorized access. The survey underscores the importance of using strong encryption standards and regularly updating encryption keys to maintain security.
Access control policies are another critical component of the DiD strategy. These policies dictate who or what can access various parts of the ICS network, thereby minimizing the risk of unauthorized intrusions. The researchers emphasize the need for stringent access control measures, including multi-factor authentication and role-based access control, to enhance security.
Intrusion detection systems (IDS) are also examined in the survey. These systems monitor network traffic for signs of malicious activity and alert administrators to potential threats. The researchers note that advanced IDS solutions, equipped with machine learning capabilities, can significantly improve the detection of sophisticated cyber attacks.
Software-defined networks (SDN) are another innovative approach to enhancing ICS security. By centralizing network management and enabling dynamic configuration, SDN allows for greater flexibility and control over network resources. The survey highlights the potential of SDN to improve network security by providing real-time visibility and control over network traffic.
The survey concludes by offering a new perspective on the latest developments in ICS network security. The researchers hope that their comprehensive review will serve as a valuable resource for industry professionals and academics alike, fostering further innovation and collaboration in this critical field.
As the threat landscape continues to evolve, the need for robust ICS network security measures becomes increasingly apparent. The insights and recommendations provided in this survey offer a roadmap for enhancing the security of Industrial Control Systems, ensuring that they remain resilient against the ever-growing array of cyber threats. By adopting a multi-layered approach to security and leveraging advanced technologies, ICS operators can better protect their networks and safeguard the critical infrastructure they support. Read the original research paper here.