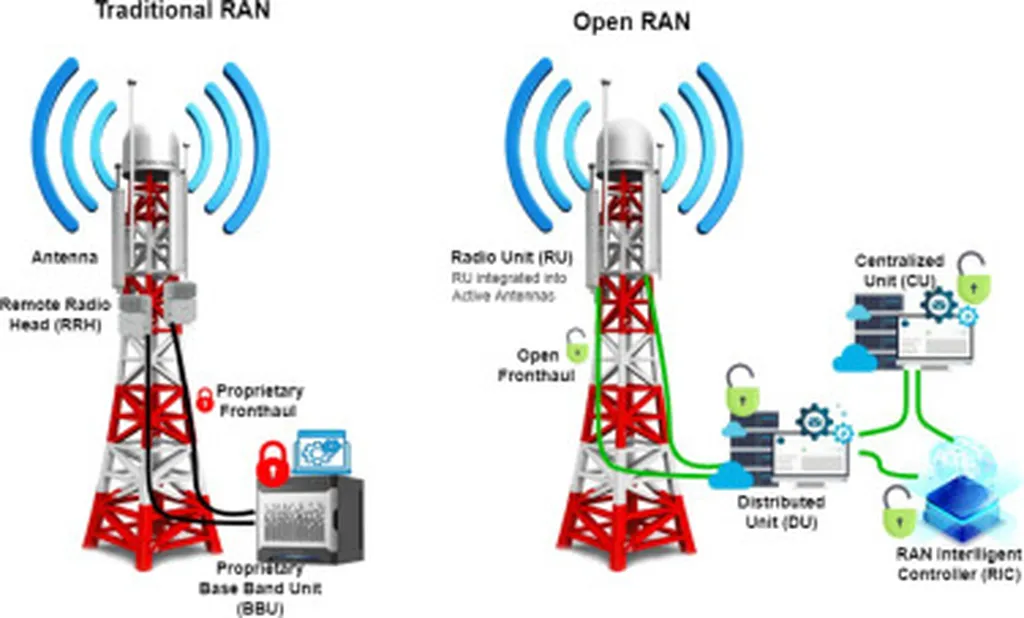
In an era where cyber threats are becoming increasingly sophisticated, securing near-real-time (near-RT) control operations in Open Radio Access Networks (Open RAN) has emerged as a critical challenge. A recent study by researchers Hamed Alimohammadi, Samara Mayhoub, Sotiris Chatzimiltis, Mohammad Shojafar, and Muhammad Nasir Mumtaz Bhutta introduces a multi-layer defence framework designed to bolster the security of near-RT RAN Intelligent Controller (RIC) operations. This framework addresses a significant gap in current security measures, which often fail to protect against runtime threats that target the control loop while the system is operational.
The researchers categorize operational-time threats into three distinct levels: message-level, data-level, and control logic-level. Each category demands a specialized detection and mitigation strategy. For message-level threats, the team developed a signature-based E2 message inspection module. This module performs structural and semantic validation of signalling exchanges, ensuring that any anomalies in communication are promptly identified and addressed. By scrutinizing the integrity and authenticity of messages, this component acts as a critical first line of defence.
For data-level threats, the researchers implemented a telemetry poisoning detector. This innovative solution employs a temporal anomaly scoring mechanism using a Long Short-Term Memory (LSTM) network. The LSTM network is particularly adept at detecting temporal anomalies in telemetry data, providing a robust defence against data poisoning attacks. By continuously monitoring and analyzing data streams, the detector can identify and mitigate anomalies in real-time, thereby safeguarding the integrity of the telemetry data.
The third layer of defence targets control logic-level threats. The researchers introduced a runtime xApp attestation mechanism based on execution-time hash challenge-response. This mechanism ensures that the control logic of the RIC remains uncompromised by continuously verifying the integrity of executing applications. By employing a challenge-response protocol, the system can detect any unauthorized modifications or malicious activities, providing an additional layer of security.
The effectiveness of the proposed framework was evaluated on an O-RAN testbed comprising FlexRIC and a commercial RAN emulator. The results demonstrated impressive detection rates with minimal latency overheads, proving the framework’s feasibility for practical integration. The safeguards operated within near-RT time constraints, significantly enhancing protection against runtime attacks while introducing less than 80 milliseconds of overhead for a network supporting 500 User Equipment (UEs).
This research lays the foundation for deployable, layered, and policy-driven runtime security architectures for the near-RT RIC control loop in Open RAN. The framework is designed to be extensible, allowing for the integration of future mitigation policies and threat-specific modules. By addressing the critical need for robust security in near-RT operations, this work paves the way for more secure and resilient Open RAN deployments, ensuring that the control loops remain protected against evolving cyber threats.
In the defence and security sector, the implications of this research are profound. As Open RAN technology continues to gain traction, the need for advanced security measures becomes ever more pressing. The multi-layer defence framework proposed by Alimohammadi and his colleagues offers a comprehensive solution to the challenges posed by runtime threats. By integrating this framework into existing and future Open RAN deployments, defence and security organizations can enhance their operational resilience, ensuring the integrity and security of their communication networks.
Moreover, the framework’s modular and extensible design allows for continuous improvement and adaptation to new threats. This flexibility is crucial in the rapidly evolving landscape of cybersecurity, where new vulnerabilities and attack vectors are constantly emerging. By providing a robust and adaptable security architecture, the research not only addresses current security challenges but also lays the groundwork for future advancements in Open RAN security.
In conclusion, the multi-layer defence framework for securing near-RT operations in Open RAN represents a significant step forward in the quest for robust and resilient communication networks. By addressing message-level, data-level, and control logic-level threats, the framework offers a holistic approach to security that can be integrated into existing systems with minimal overhead. As the defence and security sector continues to embrace Open RAN technology, the insights and innovations presented in this research will be invaluable in ensuring the safety and integrity of critical communication infrastructure. Read the original research paper here.