The rapid evolution of cellular networks has transformed them into the backbone of modern communication, supporting everything from everyday consumer applications to critical military operations. With the advent of fifth-generation (5G) and beyond 5G (B5G) networks, the Radio Access Network (RAN) is undergoing a significant shift from a closed, vendor-locked infrastructure to an open, programmable ecosystem. This transformation is largely driven by the adoption of Open-RAN (O-RAN), which allows for the deployment of control-plane applications from various sources. These applications can dynamically influence user-plane traffic in real-time, responding to emerging events and demands.
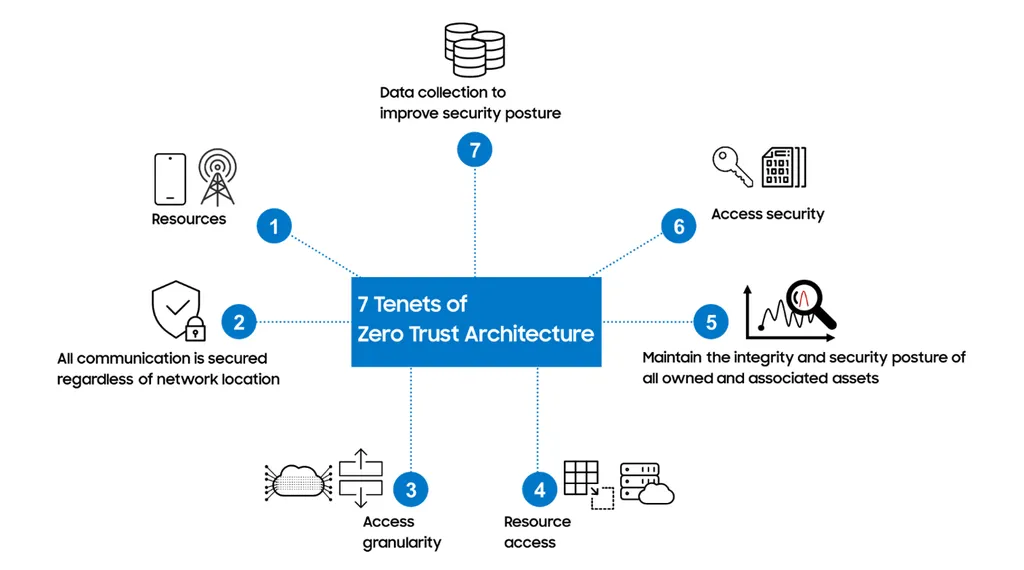
However, as cellular infrastructures become more disaggregated and software-driven, the need for robust security measures has become increasingly critical. Traditional security models, which often rely on implicit trust assumptions, are no longer sufficient. This is where Zero-Trust Architecture (ZTA) comes into play. ZTA is a security paradigm that discards the notion of implicit trust, acknowledging that threats can originate from both external and internal sources. By mandating comprehensive and fine-grained security mechanisms across both control and user planes, ZTA aims to contain adversarial movements, enhance breach detection, and improve attack response actions.
In a recent paper, researchers Charalampos Katsis, Imtiaz Karim, and Elisa Bertino explore the adoption of ZTA in the context of 5G and beyond, with a particular focus on O-RAN as an architectural enabler. The paper delves into how ZTA principles align with the architectural and operational characteristics of O-RAN, identifying key challenges and opportunities for embedding zero-trust mechanisms within O-RAN-based cellular networks.
The researchers highlight that O-RAN’s open and programmable nature presents both opportunities and challenges for implementing ZTA. On one hand, the disaggregation of network functions and the use of open interfaces enable fine-grained control and monitoring, which are essential for ZTA. On the other hand, the increased complexity and diversity of the network components introduce new attack surfaces and security challenges.
One of the key challenges identified in the paper is the need for comprehensive and dynamic authentication and authorization mechanisms. In a zero-trust model, every access request and data flow must be authenticated and authorized in real-time, regardless of whether it originates from within or outside the network. This requires advanced identity management and access control systems that can operate at scale and in real-time.
Another critical aspect is the need for continuous monitoring and real-time analytics. ZTA relies on the ability to detect and respond to threats in real-time, which necessitates sophisticated monitoring and analytics capabilities. The researchers emphasize the importance of leveraging machine learning and artificial intelligence techniques to analyze network traffic and detect anomalous behavior.
The paper also discusses the role of software-defined networking (SDN) and network functions virtualization (NFV) in enabling ZTA. SDN and NFV provide the flexibility and agility needed to implement fine-grained security policies and dynamically reconfigure the network in response to threats. By decoupling the control plane from the user plane and virtualizing network functions, O-RAN can achieve a higher level of security and resilience.
In conclusion, the adoption of ZTA in O-RAN-based cellular networks presents a promising avenue for enhancing security in the era of 5G and beyond. While there are significant challenges to overcome, the opportunities for embedding zero-trust mechanisms within O-RAN are substantial. By leveraging the principles of ZTA, cellular networks can become more resilient to both external and internal threats, ensuring the security and reliability of communication infrastructures in an increasingly connected world. Read the original research paper here.